Best Solutions to Fix High CPU Usage on macOS 10 15 Catalina
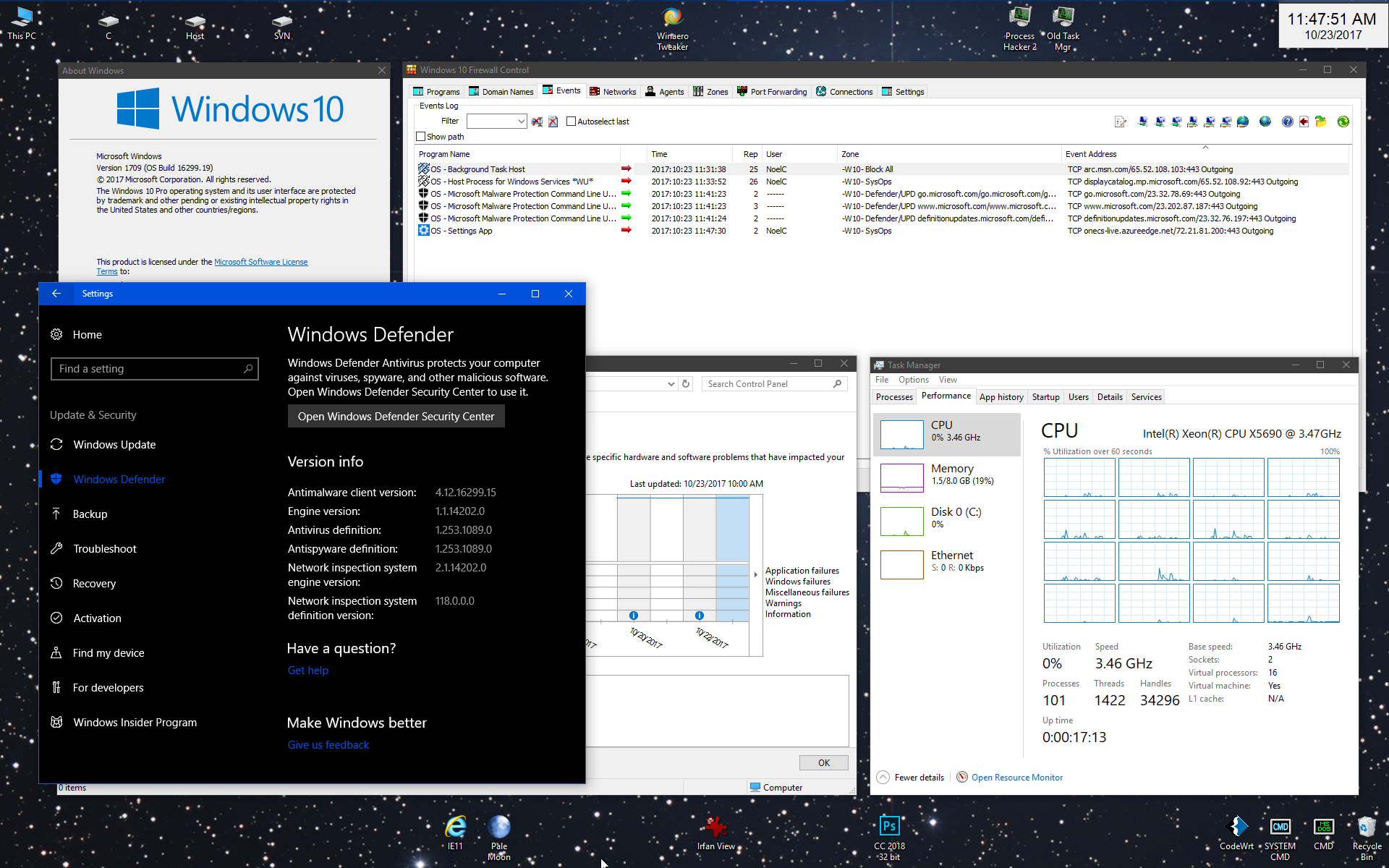
The best part is that it also adjusts your privacy settings and stops all kinds of telemetry services in the background that are responsible for eating most of the system resources. In case the system is up-to-date, there’s no harm in restarting it. This can help with random one-off issues that sometimes slow down your PC. One thing worth noting is that this is a temporary fix and you might need to look into more settings to avoid these problems from occurring again. For managed services providers, deploying new PCs and performing desktop and laptop migrations are common but perilous tasks. The adage “you’re only as good as your last performance” certainly applies. An MSP and its technicians can get everything right, complete a client’s complex cloud migrations, and perform remote work initiatives and proprietary business application upgrades, …
- Obviously, the software registry is a candidate for a persistence-capable server architecture.
- If you use resource-intensive programs like multimedia editing software, factor this into your decision and budget.
- You’d be amazed at how much more quickly your Windows 10 PC can run if you get rid of it.
- S0153 RedLeaves RedLeaves attempts to add a shortcut file in the Startup folder to achieve persistence.
- We offer Bitdefender as an example, but all antiviruses can be disabled from their menus.
If the system fails to accurately identify the hardware, it may result in inaccurate registry entries. Broken Registry Items have been the thorn in many an IT admin’s side almost since the day Microsoft introduced the Registry concept in Windows 3.1. Modern flavors of Windows tend to do a good job of maintaining the registry on their own, but there may still be some limited circumstances where broken registry items can cause issues. If you’re wondering ‘how to repair broken registry items’, read through the rest of this guide to learn what a broken registry item is, what symptoms it may cause, and how to fix it. The obvious purpose of the Registry is to act as a single repository for all configuration and setting data and remove the reliance on configuration files. B) Mac OS uses individual files much like the ini files windows used before the registry came along.
Mind you, not all the errors will pertain to the registry, but with this, you can fix issues you didn’t even know existed. Once done, let’s get to cleaning the Windows registry. All registry functions in this module which accept a handle object also accept an integer, however, use of the handle object is encouraged. This object wraps a Windows HKEY object, automatically closing it when the object is destroyed. To guarantee cleanup, you can call either theClose() method on the object, or the CloseKey() function. Restoring reflection for a key does not affect reflection of any subkeys. Will generally raise NotImplementedError if executed on a 32-bit operating system.
WinSock Proxy Service Values
Everyone has, at some point, had problems with the Photos app in Windows 10. At the same time, the Windows Photo Viewer that we know from back in the Windows 7 days did the job very well, yet it was removed with a Windows 10 update some years ago. Restart your Windows 11 device to be greeted by the old classic Start menu.
Most Common Malware Obfuscation Techniques
When using the /s switch Regedit does not return an appropriate return code if the operation fails, unlike reg.exe which does. Object Class IDs, tying them to the applications used to handle these items.
An example of how this could be used to launch malicious code. The second entry is part of a password stealing Trojan. Mind you, if the malware fails to gain admin privileges, it won’t load itself into the Run keys of HKLM. The registry Run key will have the name of IEUpdate in order to look legitimate and the second key will hide in the registry as a wallpaper. Nevertheless originate from regedit.exe, obscuring the parent process that made the change. It should be noted that there are many other run keys that can be used for this type of persistence; however, these are the most common. Persistence may also be used as a means of “cleaning up” the evidence that a malware payload was ever even there.
Boot Sequence/Order/Priority Configuration of UEFI BIOS
The order process windll.com/dll/microsoft-corporation/odbcji32, tax issue and invoicing to end user is conducted by Wondershare Technology Co., Ltd, which is the subsidiary of Wondershare group. Input “exit” and restart the computer to check if the issue has been fixed. If your computer has more than one display, click the image of the monitor you want to adjust. Change or turn off visual options so Windows is easier to see.




* Todos os comentários são de responsabilidade dos seus autores.